- Apr 25, 2015
- 1,845
- 2
- 2,199
- 327
Firstly, find the latest ISO for Kali Linux (64-bit) full - this link here should have the latest ISO links.
Register/login to your Vultr account by clicking here.
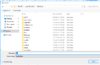
Navigate to your ISOs tab within Vultr.
Click add at the top right.
Paste in the latest full Kali (x64) e.g. https://cdimage.kali.org/kali-2019.4/kali-linux-2019.4-amd64.iso - click upload.
After waiting a few minutes, go to deploy a new server.
I select New York, $20 plan to have 4GB of RAM and then select "Upload ISO" and select your Kali ISO image.
I gave mine the hostname of veil.
Now open your server within Vultr, at the top there is a terminal icon... click.

I am going to use my arrow keys to tab down to Graphical install.
Walk through Kali installation as normal, you should eventually see:
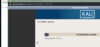
There is a chance this may take a little while as the system installs by writing disk data.
Once this finished, we are able to go about configuring our Kali environment for safe remote use.
I for example would consider setting up a VPN on a random port and firewall off everything else. Then allow port 22 connections within.
One could have full disk encryption setup, VPN into the system and be using a fairly well encrypted suite of Kali and the included tools for testing security!
I will use a network mirror:
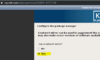
Hell yeah team!!

Now the last part will reboot your Kali system and you should be able to login as root.
Since we have relaunched, you will notice we are back to the initial install screen - this is because we now have to remove the ISO from booting:
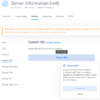
Simply go into your server, select Settings, and then Custom ISO - remove the ISO from the server.
Reload your noVNC screen and login to root:
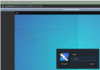
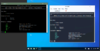
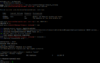
Open a terminal to edit your sshd_config:
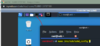
Make some important changes:
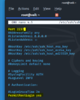
Now Ctrl+O to save the file! Press enter..
Ctrl+X to exit the file.
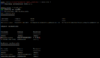
Let's start the SSH service now:
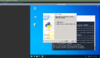
Connect to your Kali server with PuTTY now:
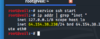
Now we know the port is 2237 (from our SSHD config) and the IP is listed above and in our Vultr panel - logging into PuTTY will be simple:
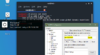
Simply click "Open" at the bottom of PuTTY once highlighted fields are filled in.
Accept the security certificate warning, Yes.
Login to your Kali root account!
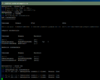
I am going to patch my Kali now:
We are ready to get some awesome shit done now!
Register/login to your Vultr account by clicking here.
Navigate to your ISOs tab within Vultr.
Click add at the top right.
Paste in the latest full Kali (x64) e.g. https://cdimage.kali.org/kali-2019.4/kali-linux-2019.4-amd64.iso - click upload.
After waiting a few minutes, go to deploy a new server.
I select New York, $20 plan to have 4GB of RAM and then select "Upload ISO" and select your Kali ISO image.
I gave mine the hostname of veil.
Now open your server within Vultr, at the top there is a terminal icon... click.

I am going to use my arrow keys to tab down to Graphical install.
Walk through Kali installation as normal, you should eventually see:
There is a chance this may take a little while as the system installs by writing disk data.
Once this finished, we are able to go about configuring our Kali environment for safe remote use.
I for example would consider setting up a VPN on a random port and firewall off everything else. Then allow port 22 connections within.
One could have full disk encryption setup, VPN into the system and be using a fairly well encrypted suite of Kali and the included tools for testing security!
I will use a network mirror:

Hell yeah team!!
Now the last part will reboot your Kali system and you should be able to login as root.
Since we have relaunched, you will notice we are back to the initial install screen - this is because we now have to remove the ISO from booting:

Simply go into your server, select Settings, and then Custom ISO - remove the ISO from the server.
Reload your noVNC screen and login to root:

Open a terminal to edit your sshd_config:
Make some important changes:

Now Ctrl+O to save the file! Press enter..
Ctrl+X to exit the file.
Let's start the SSH service now:
Code:
service ssh startConnect to your Kali server with PuTTY now:
Now we know the port is 2237 (from our SSHD config) and the IP is listed above and in our Vultr panel - logging into PuTTY will be simple:

Simply click "Open" at the bottom of PuTTY once highlighted fields are filled in.
Accept the security certificate warning, Yes.
Login to your Kali root account!
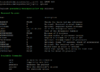
I am going to patch my Kali now:
Code:
apt update
apt upgrade -yWe are ready to get some awesome shit done now!